MouseJack Affected Devices
The following devices have been tested and are vulnerable to a MouseJack keystroke injection attack (specifically vulnerabilities that pertain to Bastille Threat Research Team Tracking Number #1-7, 9 & 12). To help determine whether you have an affected device connected to your system, please compare the following screenshots against your computer. Hardware information screens are provided for Windows, OS X and Linux for each USB dongle:
| Vendor | Affected Devices | Advisory | Vendor Response | USB ID Screenshots |
|---|---|---|---|---|
| AmazonBasics | Wireless Mouse MG-0975
USB dongle RG-0976 (USB ID 04f2:0976)) |
#7 HID Packet Injection | 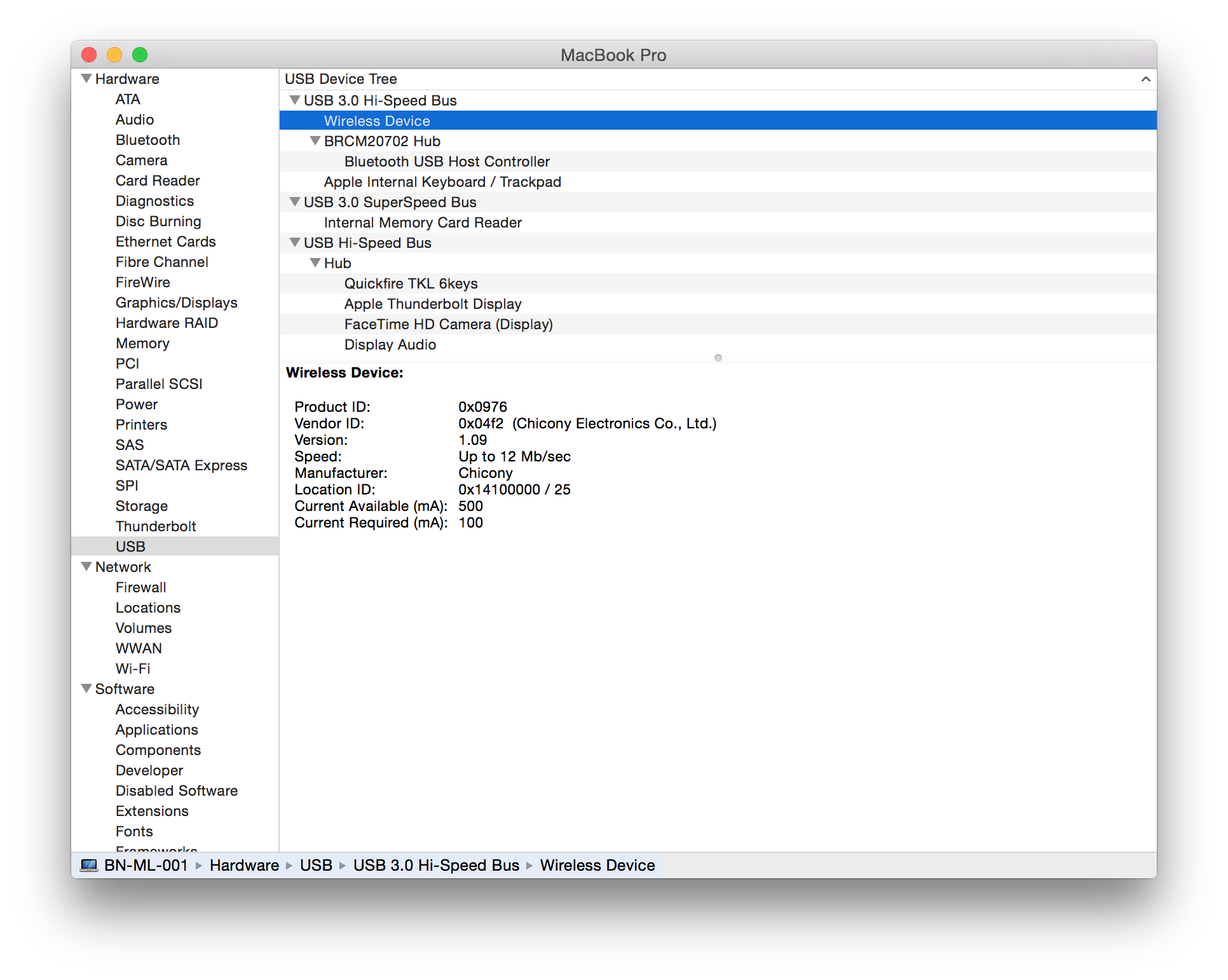 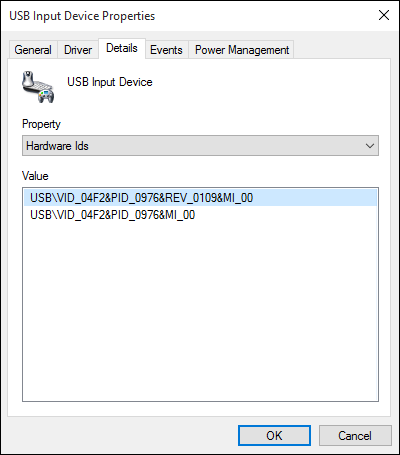 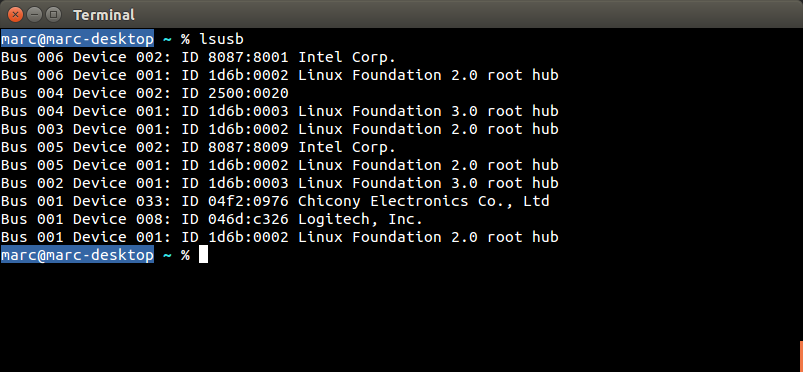 |
|
| Dell | Dell KM714 Wireless Keyboard and Mouse Combo
KM714 USB dongle (USB ID 046d:c52b) KM632 Wireless Mouse USB dongle (USB ID 413c:2501) |
#1 Force Pairing
#2 Keystroke Injection #3 Fake Mouse #7 HID Packet Injection #11 Unencrypted Keystroke Injection Fix Bypass | Statement | 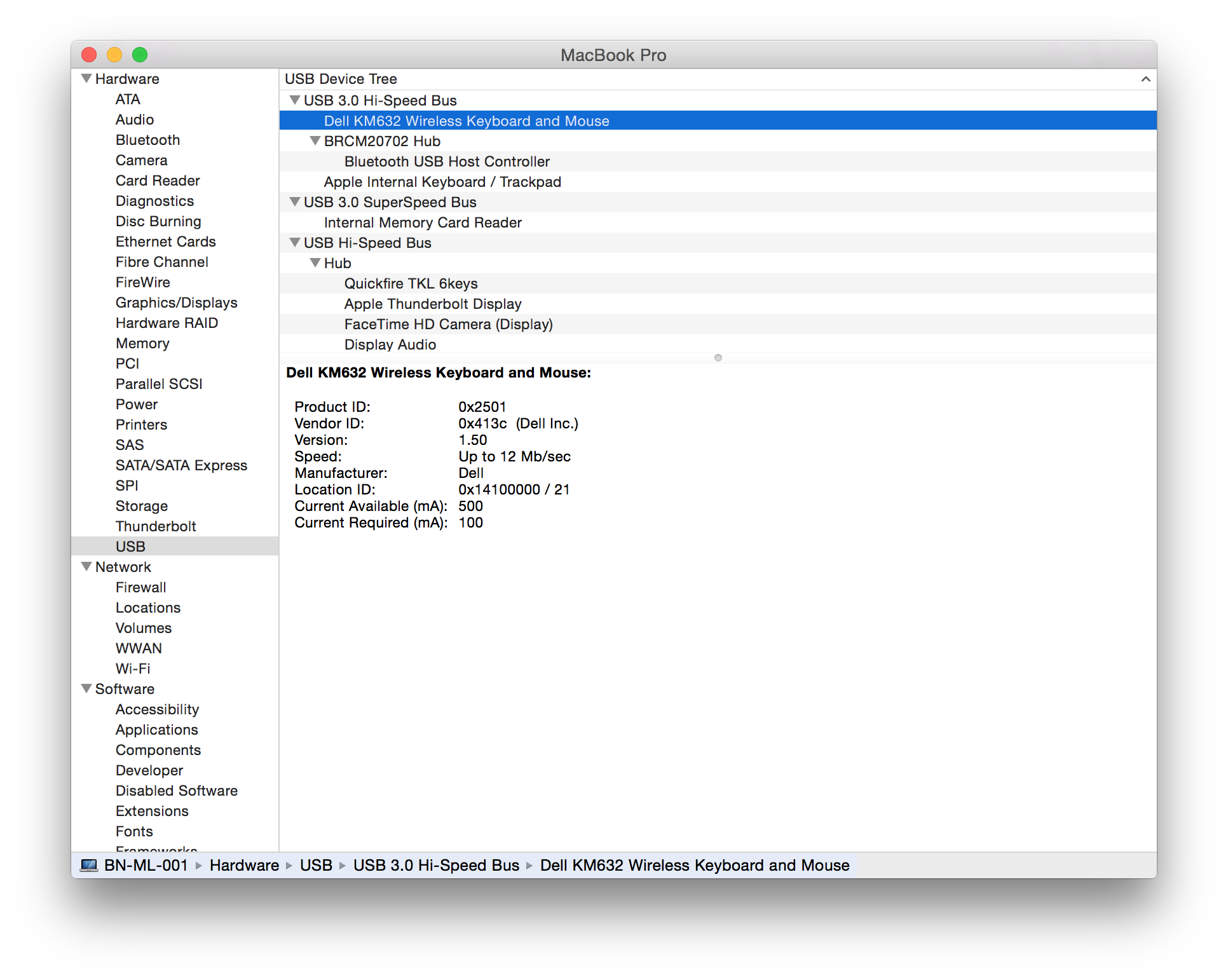 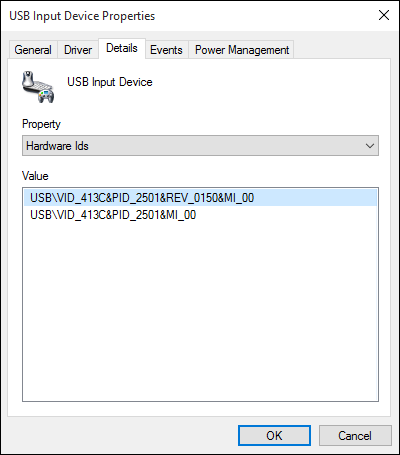 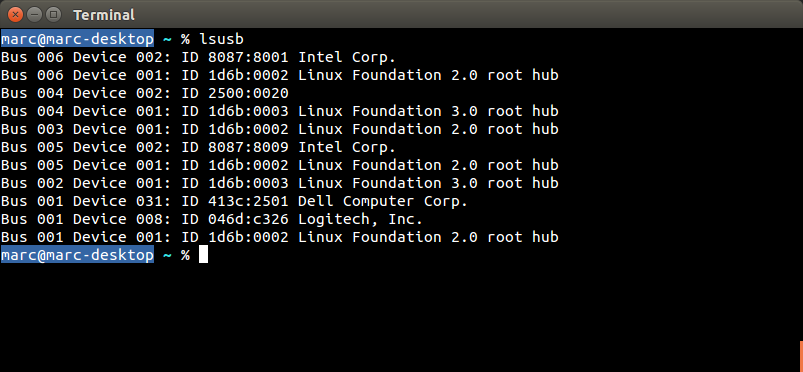 |
| Gigabyte |
K7600 wireless keyboard USB dongle (USB ID 04b4:0060) |
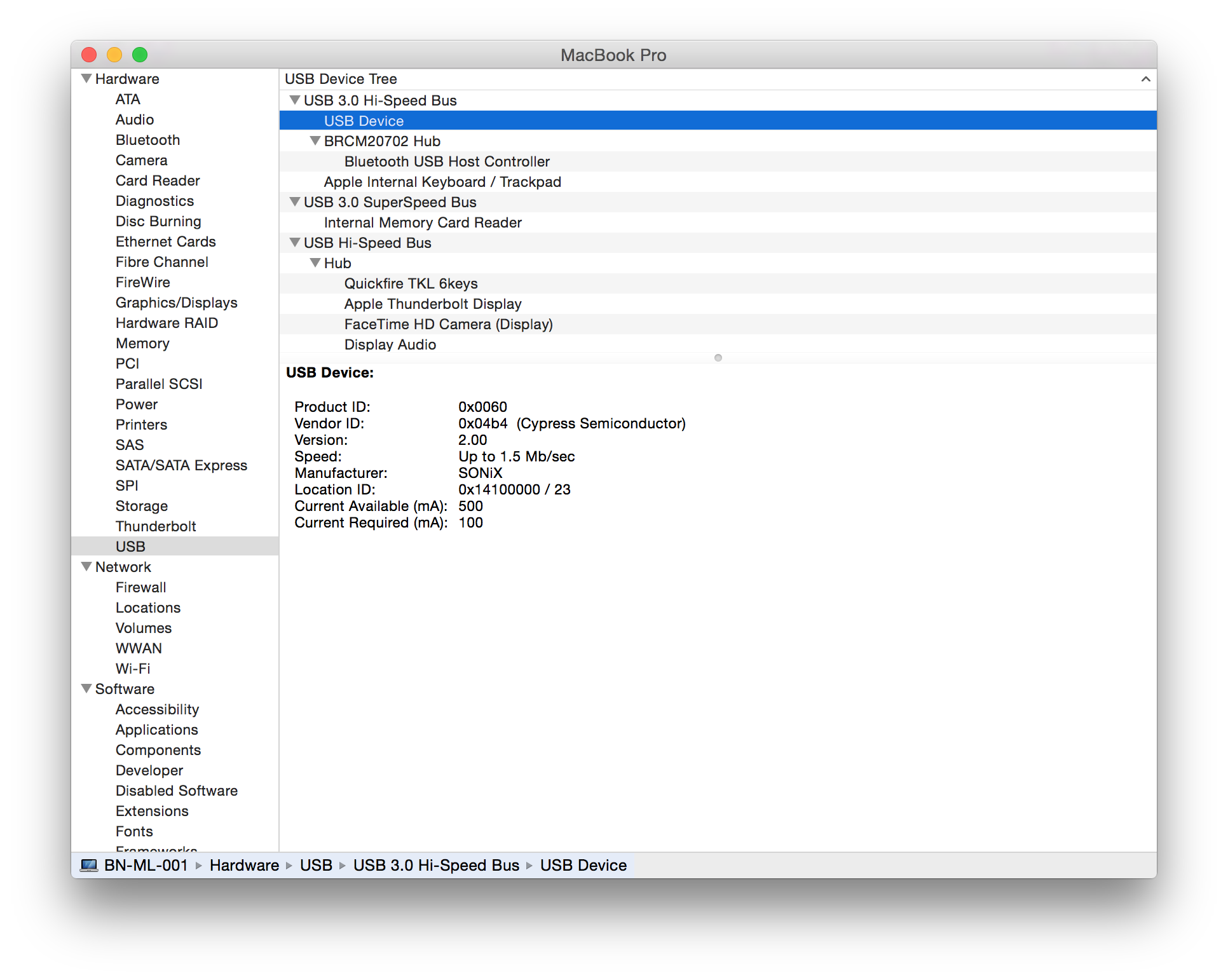 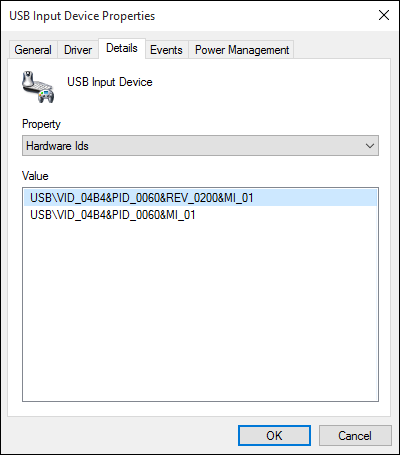 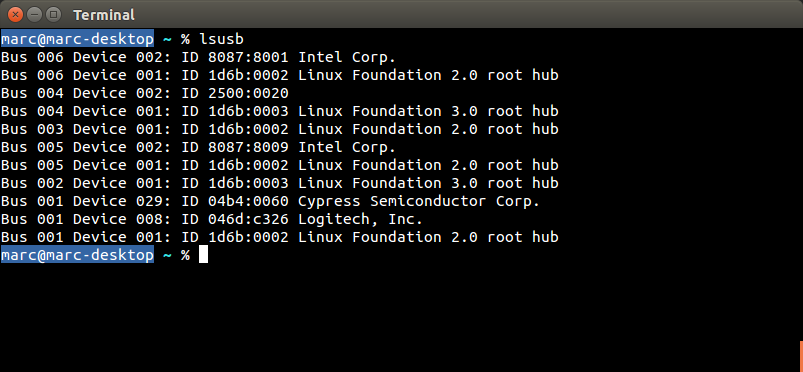 |
||
| HP |
Wireless Elite v2 keyboard Elite USB dongle (USB ID 03f0:d407) |
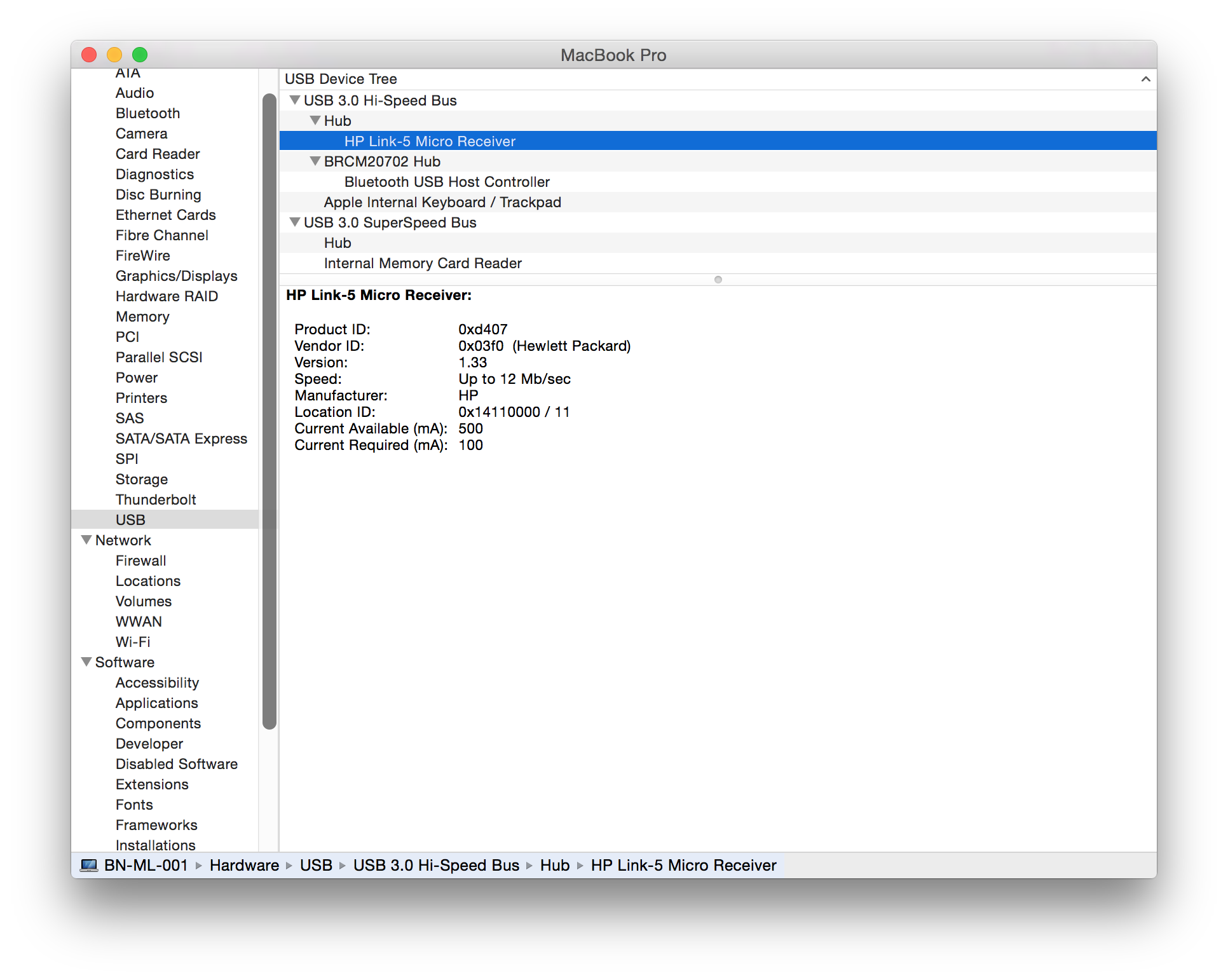 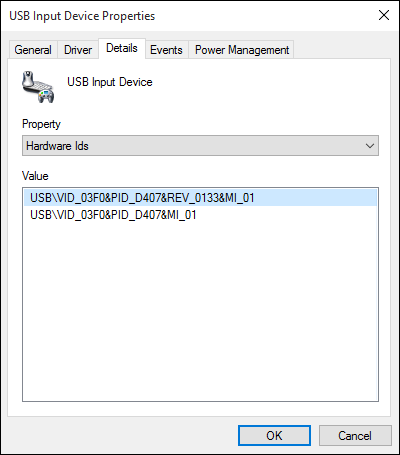 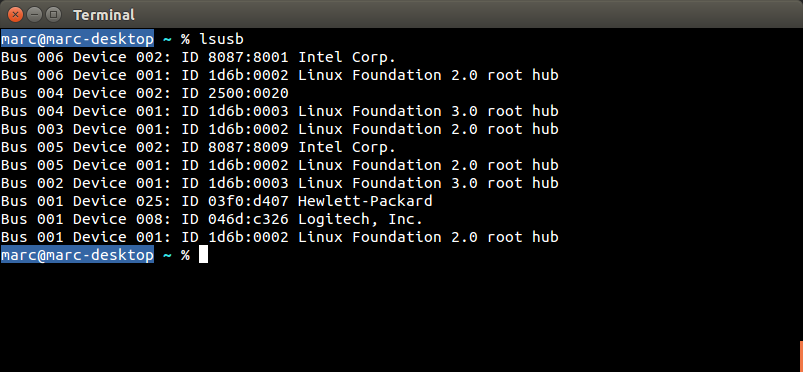 |
||
| Lenovo |
500 Wireless Mouse (MS-436) 500 USB Dongle (USB ID 17ef:6071) |
LEN-4292 | 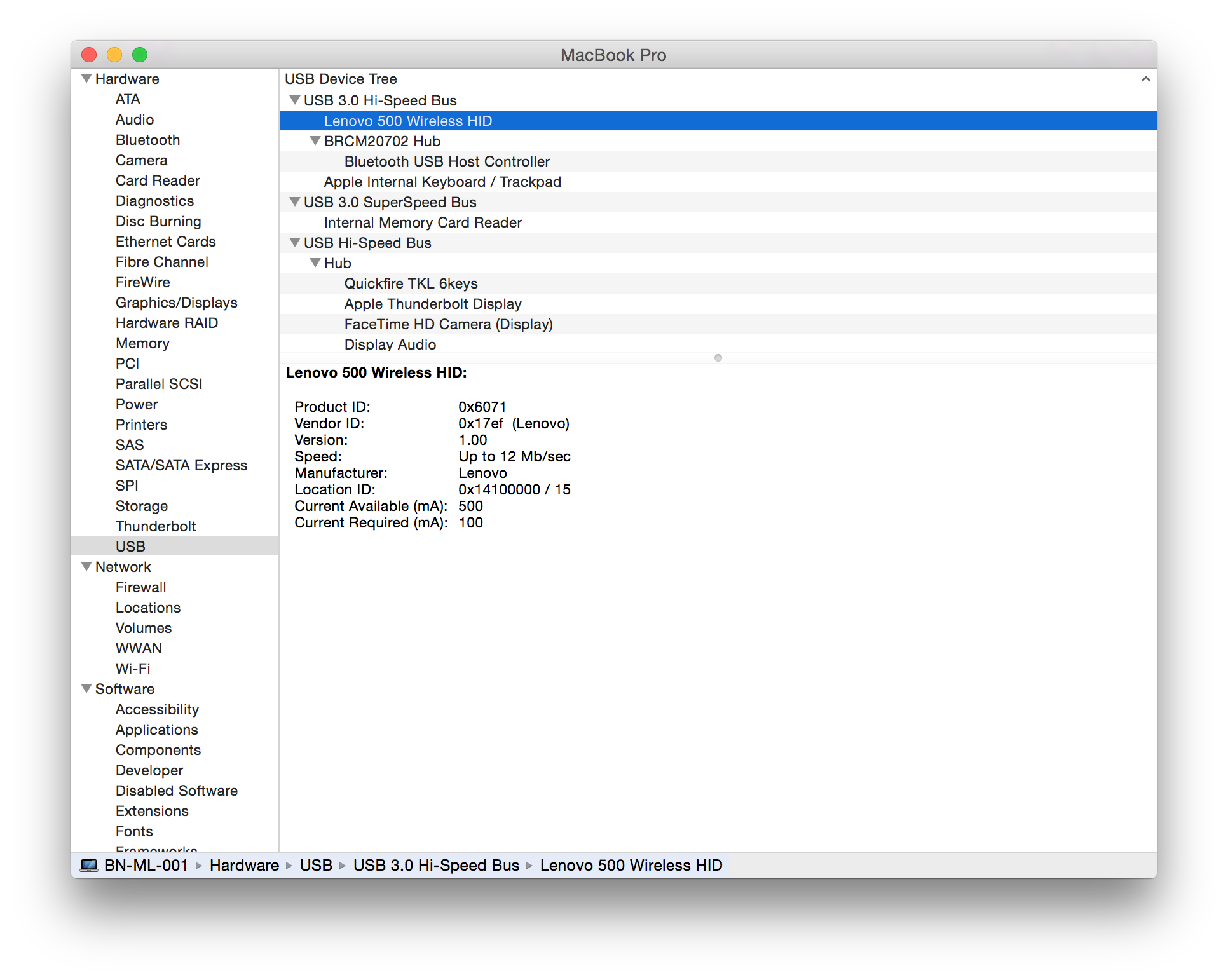 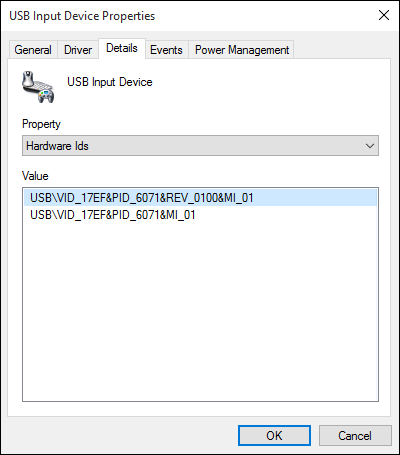 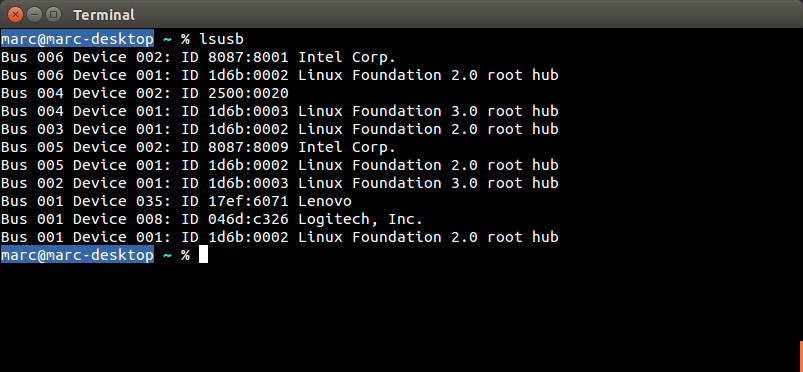 |
|
| Logitech |
K360 K400r K750 K830 Unifying dongle (USB ID 046d:c52b) Tested firmware versions:
|
(With above update, #1, #2 & #3 are solved.) |
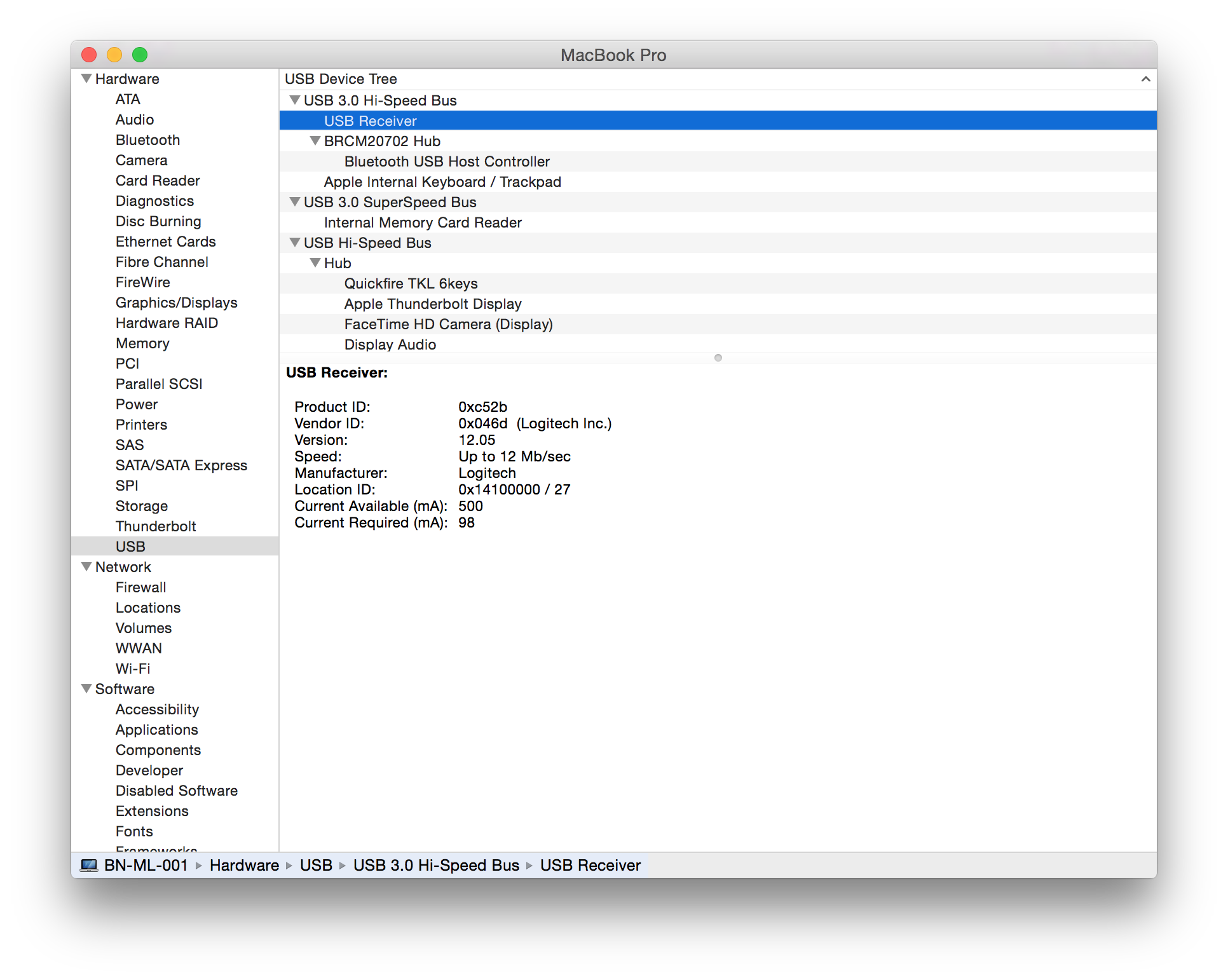 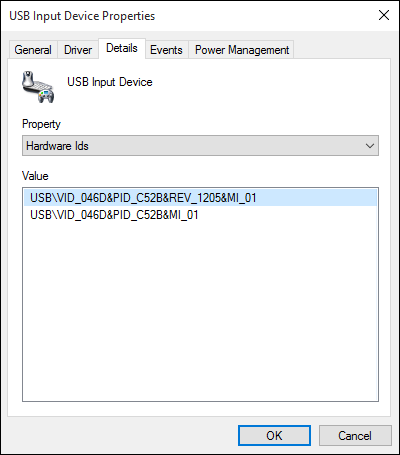 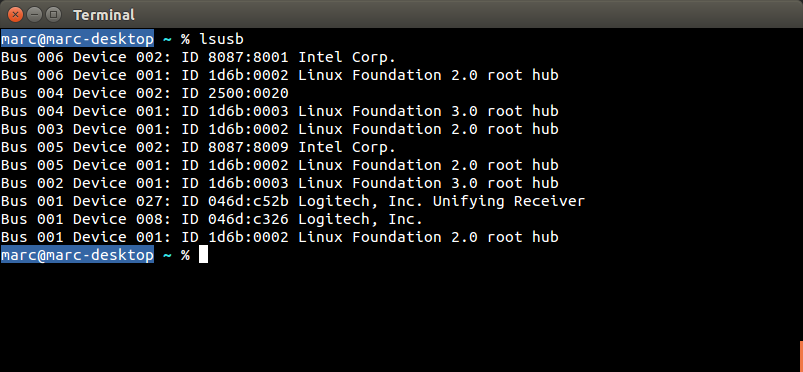 |
|
| Logitech (update) |
K400r Logitech Unifying Dongles C-U0007 (FW ver 012.005.00028) & Logitech G900 Logitech G900 dongle C-U0008 (USB ID 046d:c539) |
#11 Unencrypted Keystroke Injection Fix Bypass #12 Unencrypted Keystroke Injection #16 Malicious Macro Programming Please note: these products also affected by KeyJack. |
(With above update, #11 & #12 are solved.) | |
| Microsoft |
Sculpt Ergonomic mouse Wireless Mobile Mouse 4000 Microsoft Wireless Mouse 5000 2.4GHz Transceiver v7.0 (USB ID 045e:0745) USB dongle model 1496 (USB ID 045e:07b2) USB dongle model 1461 (USB ID 045e:07a5) |
3152550
Note: Mice part of a combo set are still vulnerable. |
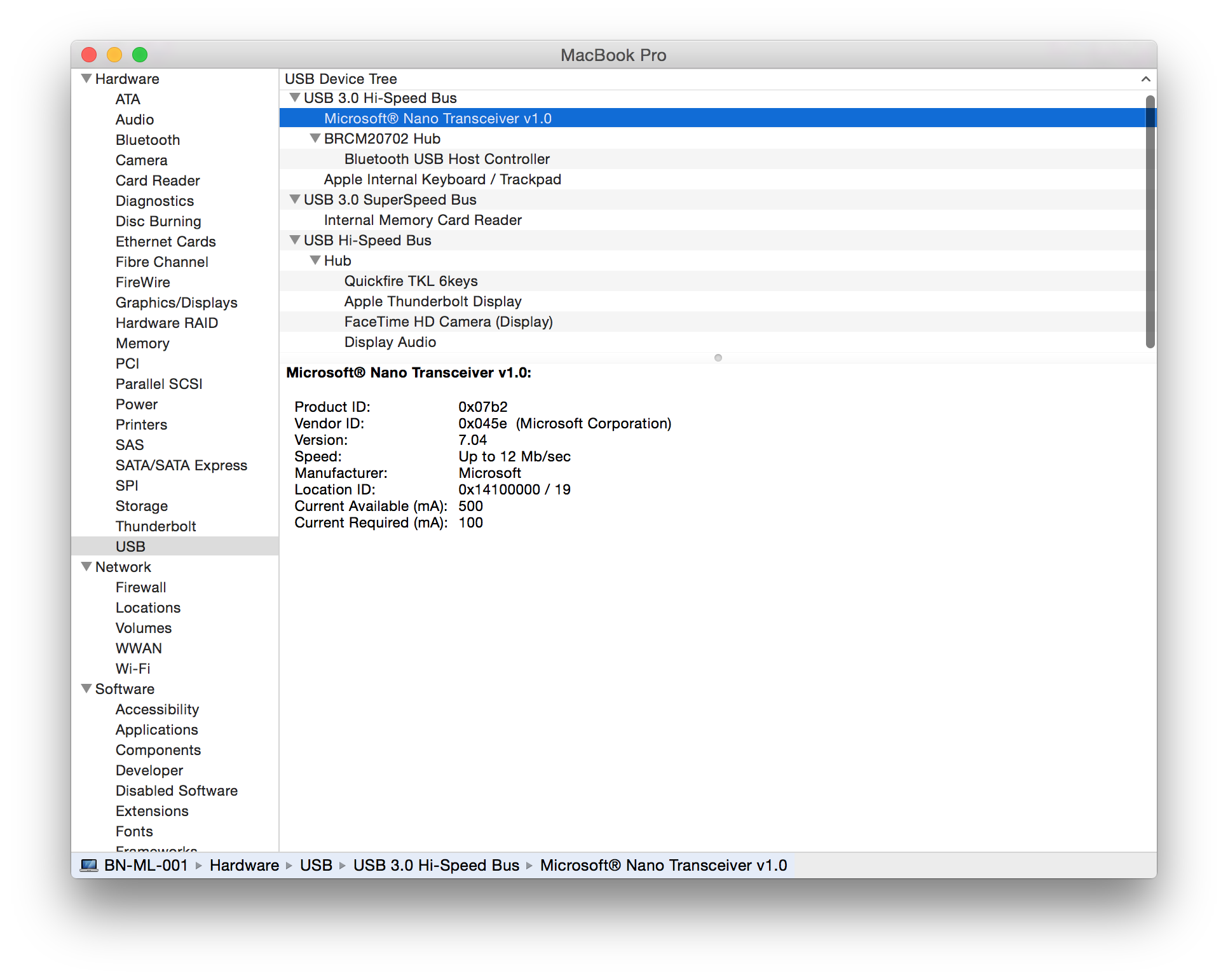 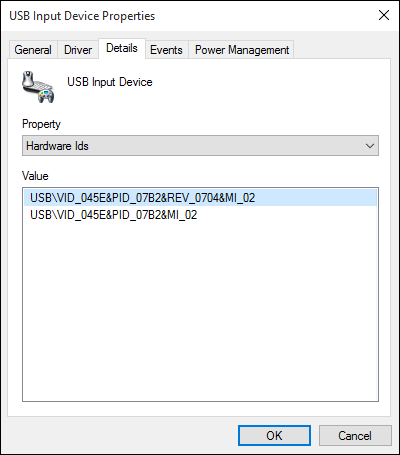 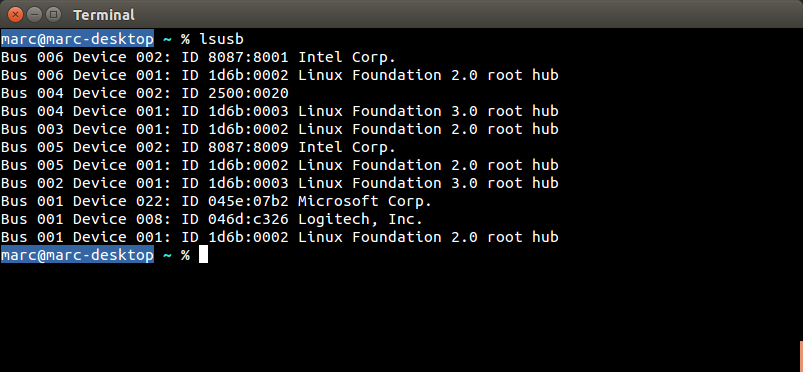 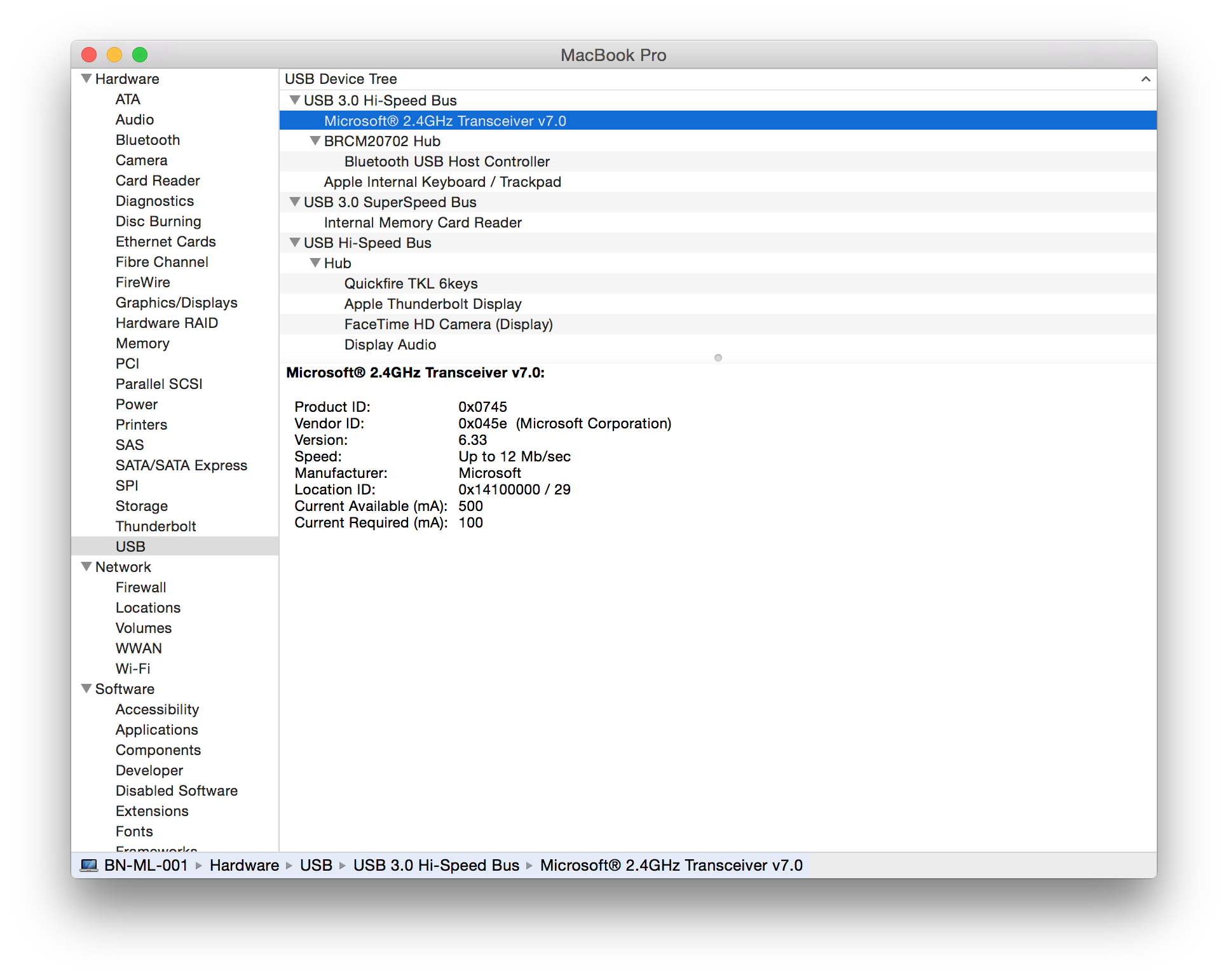 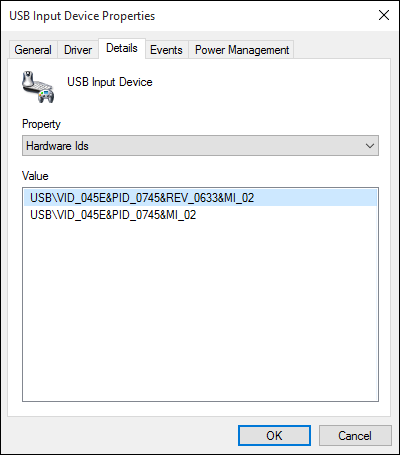 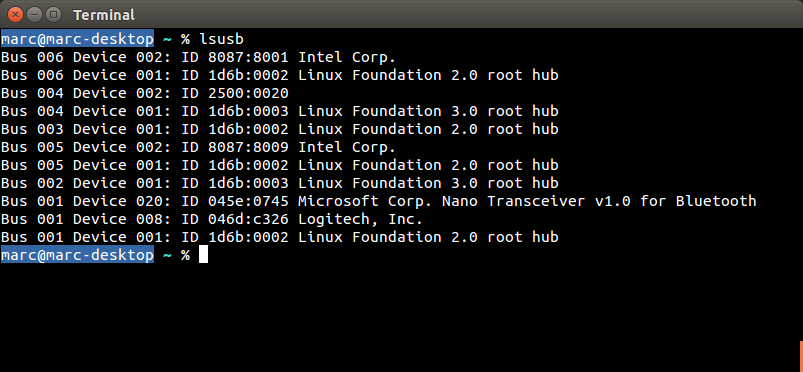 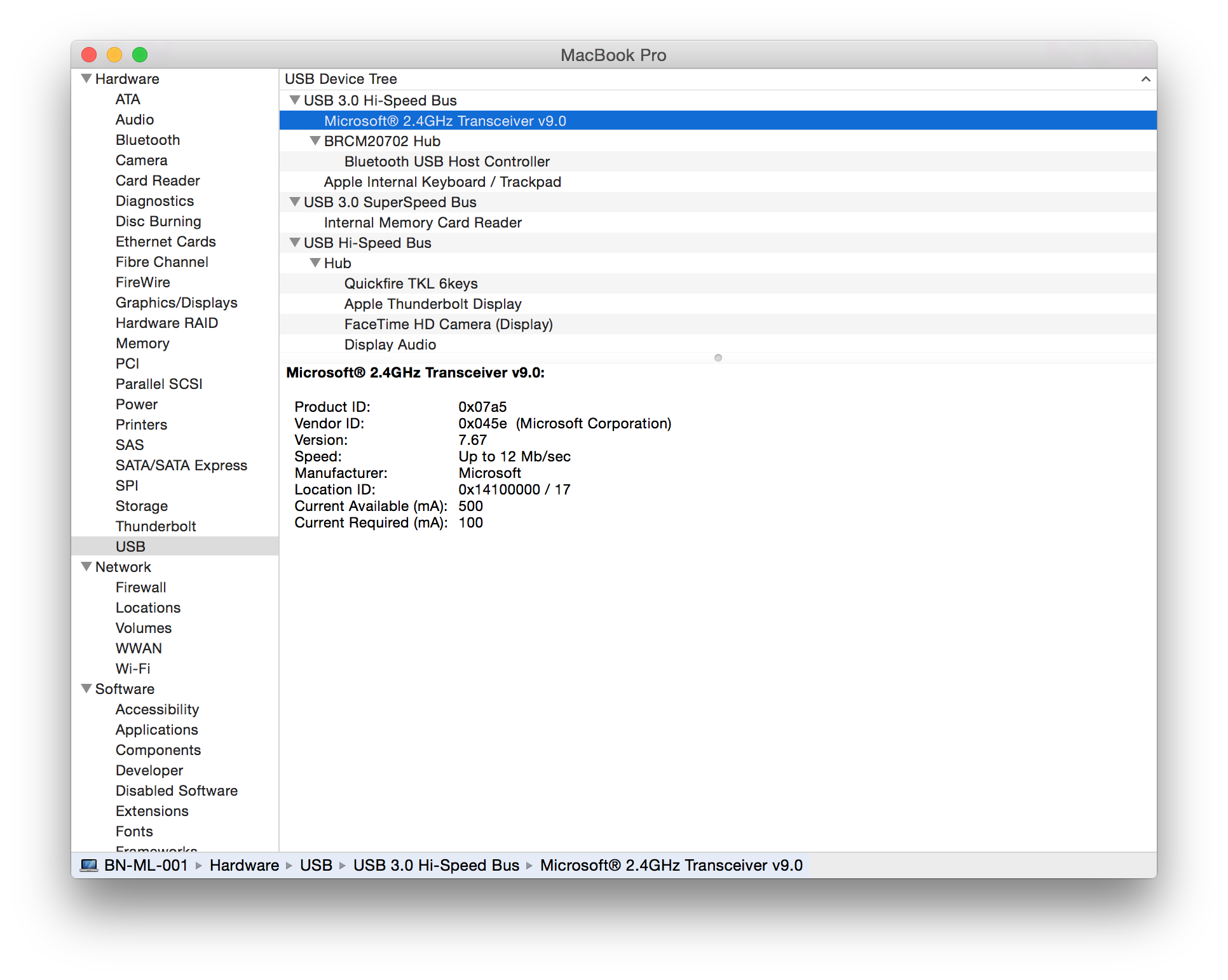 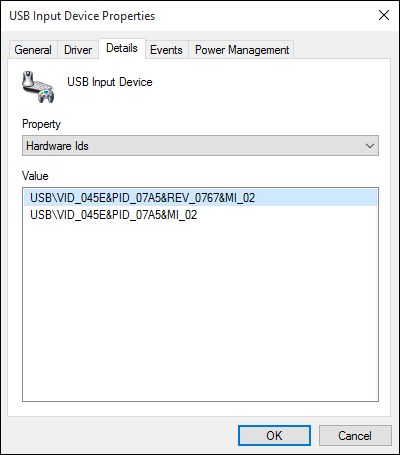 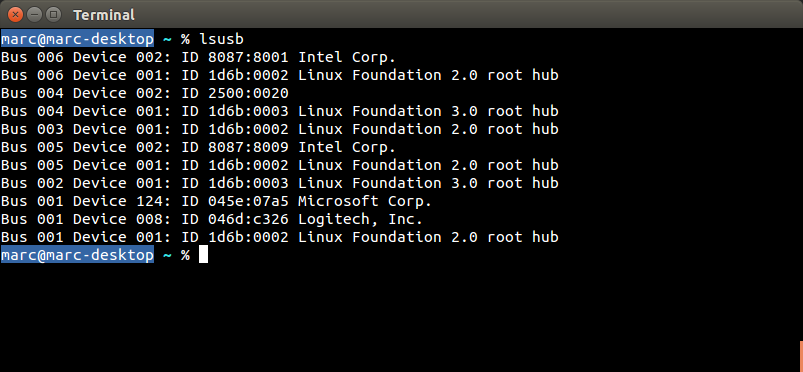 |
Note: links were updated in 2016 at time of discovery—vendors may change links without alerting us
Also covered in our advisories is a Denial-Of-Service vulnerability (Bastille Threat Research Team Tracking Number #8), which affects the following hardware:
| Vendor | Affected Devices | Advisory (with Tracking #) |
|---|---|---|
| Lenovo |
N700 Mouse N700 USB dongle (USB ID 17ef:6060) Ultraslim Keyboard Ultraslim Mouse Ultraslim USB dongle (USB ID 17ef:6032) Ultraslim Plus Keyboard Ultraslim Plus Mouse Ultraslim Plus USB dongle (USB ID 17ef:6022) |
Although the Bastille Threat Research Team endeavored to test a wide variety of models of wireless keyboard and mice from multiple vendors, it is not possible to acquire and test every model available on the market. There may be other models and vendors that are affected by this class of vulnerability, so the list should not be considered definitive.
Advisories
The plain-text advisories can be found above, and at CERT/CC VU#981271
Remediation
Immediately disconnect all affected USB dongles, and use wired keyboards and mice instead.
If you are using affected Logitech or 'Lenovo 500' devices, please update your firmware by referring to the appropriate instructions (see appropriate Vendor Response links above).
Dongles from other vendors were not found to support upgrading of firmware, so it does not appear possible to patch them. Therefore it is recommended that users contact their preferred vendor and inquire into which models are not vulnerable for future purchases.
Tools
The Bastille Threat Research Team is releasing free, open source tools to enable interested parties to discover wireless mice and keyboards that may be vulnerable to MouseJack.
Please refer to: https://github.com/BastilleResearch/mousejack


